MITM, also known as “man in the middle” is a technique to listen to traffic between two parties, in this series of articles, between a mobile app on a mobile phone and backend server(s).
Listening to the traffic between a mobile application on our mobile device, this technique
In order to utilize MITM we need to fulfill two basic criteria:
To be able to listen to the traffic is usually achieved by rerouting the traffic through a proxy we control.
To be able to decrypt the data, usually by making the device or the application to use a certificate we generated (mitm certificate) and that we own its private key.
In this article, I will focus on the latter as it is usually the most complex part.
**Note: This is not a hacking tutorial, all the techniques that will be discussed are for educational purposes only and often used for debugging and development.
Over the recent years new techniques developed to make mitm harder, especially around the certificate part, here are some of the challenges you may encounter once trying to insert and make your certificate work.
OS level restrictions, ie. in Android 10 and above, you can’t just install your certificate and assume it will be trusted - all the certificates will be installed as user certificates which automatically blocks applications from trusting it.
Application-level restrictions are usually called SSL pinning. There are a few types of SSL pinning:
Implicit - via configuration or manifest file
Explicit - by specifying inline that SSL pinning is used and which certificate is pinned.
Alternative - usually using custom or 3rd party libraries to manage certificates and cryptography.
On top of the above, additional techniques are sometimes applied for root and anti-SSL-pinning detection
Those are legitimate mechanisms that came to make it harder to abuse the applications, ie. cheating in Pokemon Go, yet when it comes to analysis and debugging it becomes a hurdle.
There is no silver bullet, one fits all, solution. In most cases, you will have to just try yourself to find out what works using the tools and techniques that will be discussed here. To summarize, here are the different levels where we can attempt to enable mitm for an application.
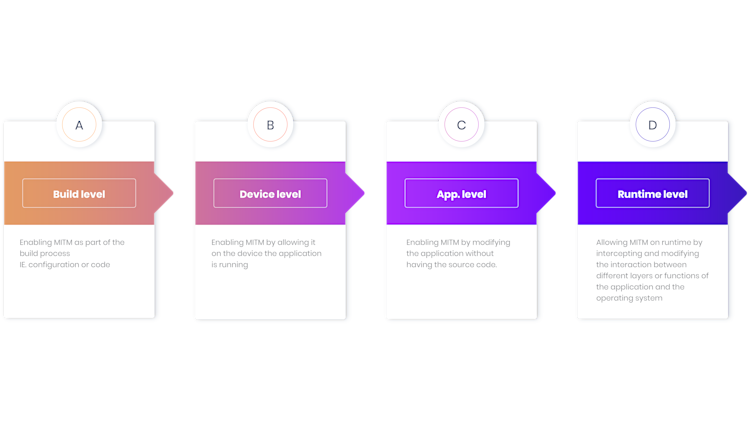
In this series of articles we will discuss the following solutions:
Building your application to accept your mitm certificate - only valid if you have the source code.
Bypassing of restriction by installing root certificate on AVD image. (Android)
Statically removing SSL-pinning via one of two methods:
Manually unpack and repack (and sign) the application after removing SSL pinning.
Use tools to automatically remove common cases of SSL pinning.
Dynamically remove SSL pinning (and more) with Frida dynamic instrumentation toolkit.
We will use Android as our model os, yet some of the techniques can be translated to ios and other OSs as well.

